Application Security - 7 Ways to Protect your Business Applications

Today's world is full of applications. Applications are available everywhere, over various networks and connected to Cloud. The Network level security is not enough to protect the application used by varieties of users, thus Application Level Protection is needed to ensure the security of the application that are used in an organization to run a day to day operations.
Let us first understand what Application Security is and why an organization needs to protect the application in first place.
Application security is the practice of ensuring that an application is protected from potential threats and vulnerabilities that could be exploited by attackers. This includes protecting the application from being hacked or compromised in any way, as well as protecting the data and systems that the application interacts with.
Application security involves a number of different practices and technologies, including secure coding practices, code reviews, testing and validation, and the use of security tools and frameworks. These measures help to identify and fix vulnerabilities in an application before it is deployed, and to protect it from threats once it is in use.
Why Should an organization need Application Security?
First of all, we need to understand that, effective application security is critical for organizations of all sizes, as applications are often the primary way that users interact with systems and data, and are therefore a prime target for attackers. If an application is compromised, it could potentially allow an attacker to gain access to sensitive data or systems, leading to data breaches, financial losses, and reputational damage. By implementing strong application security measures, organizations can protect themselves, their customers, and their data from potential threats.
Secondly, applications are becoming increasingly complex, with many modern applications relying on a combination of different technologies and integrations. This complexity can make it harder to secure an application, as there are more potential vulnerabilities that need to be identified and addressed.
Finally, the consequences of a successful attack on an application can be severe. Data breaches can lead to financial losses and damage to an organization's reputation, while a disrupted or unavailable application can impact an organization's productivity and revenue. By prioritizing application security, organizations can mitigate these risks and ensure that their applications are secure and reliable.
Here are seven ways that organizations can implement to protect their applications:
- Implement secure coding practices: Ensuring that applications are developed with security in mind is an important first step in protecting them. This includes following best practices for coding and using frameworks and libraries that have been designed with security in mind.
- Conduct code reviews: Regularly reviewing code can help identify potential vulnerabilities and ensure that applications are secure. This can be done manually, through peer reviews, or automatically, using tools such as static analysis tools.
- Test and validate: Testing and validating applications can help identify vulnerabilities and ensure that they are fixed before an application is deployed. This can include testing for common vulnerabilities such as SQL injection, cross-site scripting, and insecure authentication.
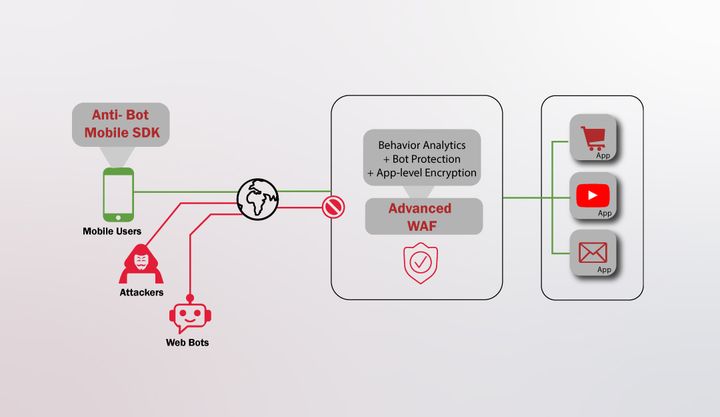
- Use security tools: There are many tools available that can help organizations identify and fix vulnerabilities in their applications. These tools can include static analysis tools, dynamic analysis tools, and web application firewalls.
- Implement secure communications: Ensuring that communication between applications and other systems is secure is critical for protecting data and systems. This can be achieved through the use of secure protocols such as HTTPS and the implementation of strong encryption.
- Monitor and log activity: Monitoring and logging activity can help organizations identify potential threats and respond to them quickly. This can include monitoring for unusual activity, such as failed login attempts or unexpected access to sensitive data.
- Regularly update and patch: Keeping applications up to date and applying patches as they become available can help protect against known vulnerabilities. This is especially important for applications that are exposed to the internet or that handle sensitive data.
In conclusion, application security is critical for protecting applications and the data and systems that they interact with from potential threats and vulnerabilities. By implementing secure coding practices, conducting code reviews, testing and validating, using security tools, implementing secure communications, monitoring and logging activity, and regularly updating and patching, organizations can effectively protect their applications and mitigate the risks associated with potential attacks.



Comments ()